Getting noticed in the cybersecurity sector is tough—especially when your audience is packed with sceptical, highly technical decision-makers. Generic SEO tactics rarely cut through, and even a minor misstep can erode trust or tank your rankings.
I've worked with cybersecurity firms who struggle to attract qualified leads, stand out from competitors, or prove their authority online. If you've faced these challenges, you're not alone—and the stakes are high, with trust and compliance always under scrutiny.
In this article, I'll break down what makes SEO for cybersecurity unique, why trust signals and technical excellence matter, and how to build authority with expert-led content. You'll get actionable strategies for keyword targeting, technical SEO, and content planning, plus tips on automation, measuring ROI, and avoiding common mistakes.
By the end, you'll know exactly how to attract high-value leads, strengthen your digital reputation, and keep pace with the industry's rapid changes—all with practical steps you can start using right away.
What is cyber security SEO?
Defining cyber security SEO
Let’s kick off with a simple question—what exactly is cyber security SEO? At its core, it’s search engine optimisation specifically designed for the complex world of cybersecurity. This isn’t general SEO; it requires a much sharper, more technical approach.
Cybersecurity is a high-stakes industry where trust and authority are paramount. Standard SEO tactics often fall short because they don’t account for the highly technical nature of the products, the sophisticated buyer journey, and the critical need for E-E-A-T (Experience, Expertise, Authoritativeness, and Trustworthiness).
It’s not about drawing just anyone to your site. Rather, you’re appealing to a highly discerning audience: think chief information security officers (CISOs), security engineers, IT managers, compliance leaders, and business decision-makers. Each comes with unique needs, decision criteria, and sky-high expectations of trust.
So how do you actually reach these experts? Here’s where keyword research gets a facelift. Generic keywords won’t work. You’ll want to target queries like “penetration testing”, “zero-day vulnerabilities”, or “security compliance audit tools.” If your content directly addresses these industry-specific queries, you become instantly more relevant to those actively seeking answers about technical threats and regulatory hurdles.
But cyber security SEO isn’t static. The landscape shifts fast—threats change, best practices develop, and compliance standards get updates. That means your content can’t gather dust. Blogs and resources on your site must be checked and refreshed frequently, or they risk becoming irrelevant.
On top of content, you need to monitor your site’s technical health. Fast performance, mobile optimisation, and a solid site structure are all non-negotiable.
And even once you’ve hit the technical mark, remember: your messaging must blend technical precision with clarity. You’re writing for both subject matter experts and less technical decision-makers who also influence the buying process.
Why cybersecurity SEO is different from general SEO
So, what really sets cybersecurity SEO apart from the usual playbook? In a word: trust. Security-focused buyers are trained to be wary. They’re searching for proof that you know your stuff and are safe to deal with.
User trust is central to her approach. 'That’s the most valuable currency,' she explains. Lose it, and it’s hard to get back.
Trust-building starts with the basics: HTTPS encryption, clear certification badges like ISO 27001 or Cyber Essentials, easy-to-find privacy policies, and current compliance statements. These cues reassure prospective clients and signal reliability to search engines—improving your rankings as a result.
Higher technical expectations go hand in hand with these trust signals. Users will abandon a slow or unsecured site without a second thought, and search engines will likely penalise you too.
To compete, your website needs strong security, quick loading times, and clear display of compliance information at all buyer touchpoints.
There’s no need to take this on faith. When one cybersecurity consultancy improved its trust signals—adding better security badges and updating privacy policies—they saw a noticeable bump in organic lead conversions. Meanwhile, a competitor with an expired SSL certificate and missing compliance details slipped in search results and saw fewer leads. Visible signs of diligence directly influence business results in this sector.
Core objectives of cyber security SEO
- Brand visibility in a competitive landscape
Get your firm noticed for key sector-specific and long-tail searches, reaching decision-makers at exactly the right moment. - Qualified lead generation
Attract risk-aware buyers with insight-rich content and optimised conversion opportunities tailored for them. - Digital authority and trust
Strengthen your brand by earning authoritative backlinks, showing thought leadership, and offering verifiable compliance credentials.
In cybersecurity, trust and visibility really do go hand in hand. Firms that focus on these areas often find themselves attracting better leads—and securing a stronger market presence. But remember, cyber security SEO is not a quick fix. It’s a constant process of improvement, demanding vigilance so your site keeps pace with both threats and client expectations.
The benefits of SEO for cybersecurity companies
Attracting qualified, security-focused leads
Let’s face it, not all leads are created equal—especially in the cybersecurity world. SEO acts as a magnet for people who are already searching for the security solutions you offer. Think about it: instead of chasing after a broad, often uninterested audience with cold emails or ads, SEO pulls in those CISOs, IT leaders, and compliance officers who are urgently seeking answers to pressing, technical problems.
Picture someone typing “cyber incident response retainer” or “GDPR cloud security” into Google. That’s not idle browsing; it’s a clear sign they need solutions, fast. By targeting these high-intent keywords, firms can massively increase both the relevance and quality of incoming enquiries. And here’s the kicker—a shift from scattergun outreach to focused SEO often means conversion rates surge as much as 40% compared to old-school marketing. That’s the power of meeting your prospects exactly where their needs are.
Establishing authority and building digital trust
In cybersecurity, trust and authority aren’t just nice to have—they’re non-negotiable. When your website hosts expert guides, timely compliance updates, and detailed risk assessments, you’re doing more than just answering questions. You’re building your firm’s reputation as an industry leader.
It doesn’t stop there. If major industry players link to your content and you show up high in search results, your authority gets a natural boost. And don’t underestimate the power of visible trust signals like HTTPS, credible security badges, and up-to-date privacy policies—these reassure both visitors and search engines. When you keep your compliance credentials and incident response information transparent, especially during crisis moments, you’re basically proving your reliability when it matters most.
Competitive differentiation and cost advantages
Trying to stand out in the crowded cybersecurity market? Strategic SEO puts you ahead of the curve—especially if you’re quick to optimise for new threats, regulations, or technologies before your rivals. That often translates into a sizeable spike in organic traffic and higher keyword rankings; some firms see a 35–60% growth in visitor numbers after just one year focusing on SEO.
There’s another twist. Unlike paid search campaigns, SEO’s value compounds over time—you keep reaping benefits long after the initial push. And the audience it attracts? Typically more sceptical of traditional ads, they trust organic search results far more. For cybersecurity companies, this credibility is gold dust. Over time, the cost efficiencies stack up, channelling a steady stream of high-quality leads and delivering sustainable growth—no huge ad budgets required.
Unique SEO challenges in the cybersecurity industry
Navigating long, complex buyer journeys
Let’s be honest—buying cybersecurity isn’t like choosing office supplies. The process is layered, messy, and pulls in decision-makers from every corner: CISOs, IT managers, compliance leads, plus finance and procurement. Each has their own priorities and pain points.
From the first Google search to a signed contract, research stops add up quickly. Early on, search terms might be “phishing attack trends” or “cyber risk assessment template.” As the decision nears, queries shift to “GDPR-compliant MDR providers” or “security operations centre comparison UK.”
To win visibility, your SEO must land perfectly at each touchpoint. And here’s the challenge—cybersecurity never stands still, so content and keywords require constant refreshing to stay relevant and authoritative.
Meeting compliance and regulatory expectations
This sector may just hold the record for most acronyms—GDPR, CCPA, HIPAA, and countless others aren’t optional. Your website must show privacy policies, cookie consent, and clear data transparency.
Not only is this a legal requirement, it’s also a trust signal for users and search engines. Let anything slip—even one outdated privacy notice or missing opt-out—trust takes a hit and you’ll tumble in search rankings.
And making things trickier, strict privacy controls often reduce analytics for optimising SEO. Your fallback? High-value, transparent content. If a consultancy fails to update a cookie policy after law changes, visibility drops, trust wavers, and you risk regulatory action.
Maintaining trust and technical excellence
In this space, trust is non-negotiable. Any technical slip—an expired SSL certificate or malware warning—can hit your rankings and stain your brand longer than you’d imagine.
Recovery moves slowly. Even with swift remediation, regaining your position may drag on for months.
The only real solution? Relentless technical upkeep and expert, up-to-date content. That’s how you show your dependability to both prospective clients and search engines.
Addressing scepticism and information overload
Cybersecurity professionals are, by nature, highly sceptical. They’re already inundated with dense content. Filling pages with jargon won’t cut it.
Clarity is vital, especially for non-technical decision-makers. Yet, you still need depth to satisfy the experts.
An effective approach? Offer executive summaries, define terms at the outset, and split technical deep-dives from broader business insights. Schema markup and smart internal links will boost SEO and help visitors find the right info, fast.
Ignore these, and high-quality leads will bounce. That’s when brand authority suffers.
Summary Data Table: Unique SEO Challenges
| SEO Challenge | Key Issues | Impact if Ignored |
|---|---|---|
| Complex Buyer Journeys | Multiple stakeholders; stage-specific info required | Missed opportunities; low lead conversion |
| Compliance & Regulation | GDPR, HIPAA, CCPA; onsite privacy signals | Ranking drops; trust/reputation loss |
| Trust & Technical Excellence | SSL, malware checks, authoritative content | SEO penalties; long-term reputational damage |
| Audience Scepticism & Overload | B2B scepticism, content clarity, technical/biz mix needed | High bounce rates; weaker brand authority |
Every one of these hurdles calls for close teamwork between marketing, security, and compliance. Get it right, and what once looked like an obstacle becomes your greatest SEO strength in the cybersecurity world.
Cybersecurity SEO strategies and best practices
On-page and technical SEO essentials
Let’s begin with the basics: technical SEO. In cybersecurity, a secure, high-speed website isn’t just preferred—it’s demanded. Prospects and search engines are primed to ditch anything that seems slow or unsecured.
- Core Web Vitals: speed and mobile
Your site must load quickly and work perfectly on mobiles. A laggy experience raises red flags for searchers and buyers. - HTTPS and technical security
SSL/TLS is a must. Keep security headers tight and run frequent vulnerability scans to avoid disasters from breaches or certification lapses. - Sector-specific technical pitfalls
Things like expired SSL or missed security patches instantly drop trust—and your search rankings. - From technical to content
A strong tech foundation is what lets expert-led content shine and instils real credibility.
A single technical error could cost you the audience’s trust—before your message even gets a look in.
According to Google’s latest benchmarks, the probability of a user bouncing increases by 32% as page load time goes from 1 to 3 seconds.
Content strategy: Authority, EEAT, and relevance
Now, about content—this is where cybersecurity SEO gets interesting. Google holds these sites to a higher benchmark, measuring EEAT: Experience, Expertise, Authoritativeness, and Trustworthiness.
- Expert-created, up-to-date content
Only publish advice checked by qualified professionals. Outdated info erodes your brand faster than anywhere else. - Long-tail, high-intent keywords
Nail the phrases buyers use—“ransomware response process” beats broad, generic queries every time. - Real-time updates
Fast, insightful threat analysis grabs top rankings and authoritative backlinks. - EEAT for YMYL queries
Display credentials and regulatory know-how front and centre—search engines notice when you do.
Timeliness is pivotal. Being first to break down a new threat or regulation can set you up as the market authority.
Link building and off-page considerations
Authority isn’t built in isolation. Trusted backlinks from respected industry sources have amplified weight in this sector.
- Earn top-tier backlinks
Get featured by industry leaders—through whitepapers, research, or event panels. These endorsements are SEO gold. - Avoid poor links
Spammy or irrelevant directories undermine trust; recovery can take ages. - Thought leadership presence
Share your expertise on influential channels; this fuels your authority and attracts the right visitors.
Remember, quality beats quantity every single time.
User trust signals, schema, and engagement
Trust is tangible. Cybersecurity buyers need visible, immediate signs that your site is legitimate, safe, and credible.
- Schema for credibility
Highlight accreditations and awards right in search results to instantly boost trust. - Streamlined UX and CTAs
Make site navigation logical and calls-to-action clear—security-focused prospects expect nothing less. - Avoid engagement pitfalls
Complicated menus and weak links drive risk-averse users away fast.
Schema markup and a seamless experience let you prove your value in seconds.
Summary: Best practice checklist
Here’s the quick-hit playbook:
- Solid technical SEO
Prioritise speed, strong security, and mobile optimisation. - Authoritative, current content
Everything should be expert-driven and kept up to date. - Strategic keyword focus
Target high-intent, sector-specific queries. - Quality industry links
Build respect with trusted endorsements only. - Flawless schema and UX
Audit navigation and calls-to-action for clarity and impact.
Master these steps, and you won’t just rank—you’ll set the pace for trust, leads, and lasting industry authority in cybersecurity SEO.
How website security impacts SEO performance and trust
Security as an SEO ranking and reputation factor
Here’s the truth: website security isn’t just a back-office checklist—it’s central to both your SEO results and reputation. Google rewards sites with HTTPS, yet even a seemingly minor slip—like an expired SSL certificate or mixed-content warning—sends up red flags. If visitors see a “Not Secure” message, about 30% will leave instantly, especially if your brand isn’t prominent.
Now, if malware strikes or there’s a phishing breach, the consequences multiply. Search engines may blacklist your site, wiping out rankings and visits overnight. Remember the Equifax incident? Their SEO and reputation plummeted in days. Worse still, when partners retract backlinks, every bit of hard-earned search equity starts vanishing.
Key Security Issues and Their Impacts
| Security Issue | SEO Impact | Trust Impact |
|---|---|---|
| Expired SSL or HTTPS errors | Lower rankings; browser warnings | Loss of buyer trust; high bounce rates |
| Malware/breach | Blacklisting; lost backlinks | Reputation damage; business loss |
| Outdated trust signals | Negative ranking signals | Doubt about company diligence |
Trust signals that matter for cybersecurity firms
Cybersecurity buyers dissect trust signals—probably more so than any other sector. Visual cues like ISO 27001 and Cyber Essentials certifications, current privacy policies, and visible badges shout credibility. These aren’t window dressing: they help turn sceptical visitors into real leads.
- Smart badge placement
Put badges, certifications, and seals front and centre—headers and next to forms are key reassurance zones. - Up-to-date policies
Display ‘Last Updated’ dates and keep compliance statements clear and current for confidence at a glance. - Automated monitoring
Automated checks make sure certificates never lapse—preventing surprise trust breakdowns. - Additional trust builders
Place bios, testimonials, and expert articles right where decision-makers linger.
Blend technical security with these visible trust signals and SEO best practice, and you’ll see higher rankings, better reputation, and improved conversion. For cybersecurity firms, trust is meaningless without rigour—and true rigour, in this world, is always visible.
Building an effective content strategy for cybersecurity SEO
Identifying audience and intent in cybersecurity
Building an effective cybersecurity content strategy starts with knowing exactly who you’re talking to. Is your audience stacked with CISOs and IT leaders craving technical depth, or are business executives their key decision-makers? Getting this mix right decides how much detail—and what tone—each piece of content needs.
It's not just about who’s searching, but why. That’s where keyword funnel mapping steps in. You’ll want to link broad or technical search terms to specific stages of the buyer journey—from early awareness right through to final decision. Targeting searcher intent at every step makes your content as relevant as possible, not just visible.
And let’s not overlook long-tail queries. In cybersecurity, those highly specific searches—think “GDPR-compliant incident response template”—are gold. They rank faster, bring in more laser-focused leads, and address the real pain points your prospects are battling with.
- Segmenting the audience
Distinguish technical roles (CISOs, IT leaders) from business executives to shape messaging and detail required. - Keyword funnel mapping
Link broad/technical/branded keywords to awareness, consideration, and decision stages—aligning searcher intent at each step. - Long-tail and queries
Target specific, high-intent searches for fast ranking and to address precise cybersecurity pain points.
Crafting and maintaining high-authority content
The next piece of the puzzle? Building out content that not only educates, but reassures. Cybersecurity professionals are quick to spot flimsy guidance, so everything you publish should be led by bona fide experts. Proudly display their credentials—this is one sector where authority genuinely matters.
Content clusters are instrumental here. By grouping related guides, explainers, and use-case pages together, visitors can find answers faster while search engines see you as a go-to authority.
Don’t forget evergreen assets either. Regularly updated pillar pages, like compliance handbooks or risk assessment templates, stand the test of time both for SEO and inbound enquiries.
Keeping this ecosystem healthy takes ongoing effort. Routine audits help cull anything outdated, while analytics show you exactly where to double down or trim away.
And if you want to boost engagement? Weave in webinars, infographics, or quick expert interviews—sometimes a visual or a voice says more than a blog ever could.
- Expert-led creation
Ensure all technical content is produced or reviewed by recognised cybersecurity professionals, and display author credentials. - Content clusters
Group pages by theme—guides, practical explainers, use-cases—for authority and improved navigation. - Evergreen assets
Develop regularly updated pillar content—like compliance guides and process templates—that hold long-term SEO value. - Routine content audits
Schedule systematic reviews and updates to keep content accurate and remove outdated material. - Track and refine
Use analytics to prioritise updates, consolidate assets, and guide topic expansion or content retirement. - Use multimedia
Embed webinars, infographics, or video interviews to increase engagement and showcase live expertise.
Enforcing EEAT in cybersecurity topics
Now, to truly excel, your strategy has to shout EEAT—Experience, Expertise, Authoritativeness, and Trustworthiness. Start by highlighting author bios, credentials, and professional affiliations right up front. That transparency sets you apart from the rest.
Back up your claims with real-world stories—case studies, testimonials, or true incident response recaps show you’re not just theorising, you’re delivering in the field. Citing regulators and frameworks like ISO or NCSC further strengthens your credibility for a cyber-savvy audience.
Let’s not forget the trust signals that matter most: lock down HTTPS, polish those load times, and throw privacy compliance and certification badges right where visitors can see them. A touch of schema markup helps surface these credentials directly in search results, getting you noticed by both human and algorithmic eyes.
- Showcase expertise
Prominently display author bios, credentials, and industry affiliations for full transparency. - Evidence claims
Support statements with real case studies, testimonials, or incident response stories. - Reference standards
Cite industry frameworks or regulators (e.g. ISO, NCSC) to build credibility, avoiding excessive academic referencing. - Display trust signals
Maintain HTTPS, fast load times, privacy compliance, and visually highlight certifications/badges. - Schema markup
Use schema to highlight credentials, certifications, and compliance for enhanced search visibility.
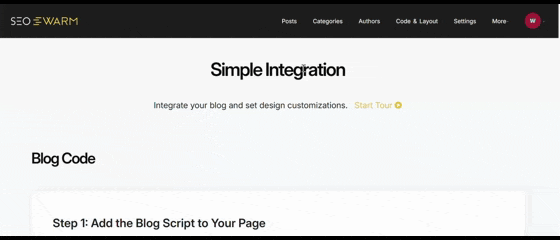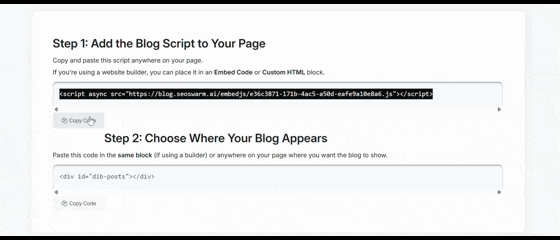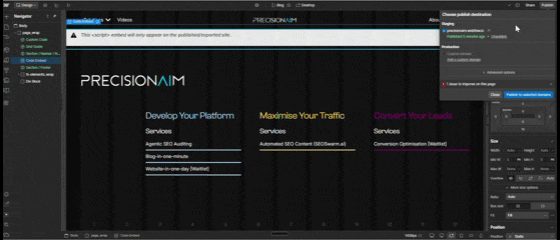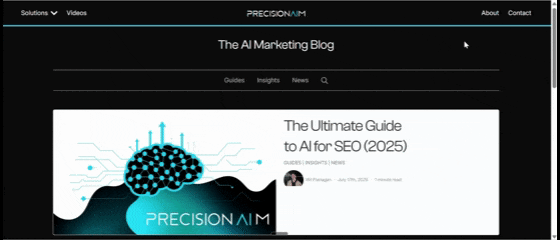
Blog-in-one-minute
Add a fully SEO-optimised blog to your website with just 2 lines of code.
AI and automation in cybersecurity SEO: Opportunities and pitfalls
How AI streamlines SEO and content for cybersecurity
AI has truly transformed cybersecurity SEO. Now, the right tools automate everything from keyword research to technical checks and compliance tracking. The laborious process of manually updating content or running periodic audits is becoming a thing of the past.
When new threats or regulations emerge, automation pushes out relevant articles and guidance at speed. Your site stays authoritative and current—without overwhelming your experts with endless admin.
This means technical teams can concentrate on strategic work. With content production quicker and compliance updates handled automatically, your business remains agile, adapting instantly as the industry shifts.
Pitfalls of automation and maintaining quality
But there’s another side to this shiny new coin. When AI misreads a law or overstates a minor risk, it opens you up to legal or reputational headaches.
Automated tools sometimes output generic or outdated advice by missing sector nuance. Some sites relying too heavily on AI have published guidance based on rules that changed—earning themselves regulatory surprises.
That’s why human oversight is essential. Only properly qualified cybersecurity professionals can catch technical subtleties and guarantee advice is both accurate and relevant. Automation is powerful, but expert judgement must remain at the forefront.
Overview of SEOSwarm by Precision AI Marketing
How do you harness that power safely? SEOSwarm is purpose-built for cybersecurity, marrying automation with sector discipline.
It covers technical SEO, ongoing audits, automated compliance tracking, instant content refreshes, and real-time threat intelligence. Unique ‘swarm intelligence’ adapts your site immediately to regulatory or risk changes.
For cybersecurity firms, this means reliable, timely content and technical leadership—without drowning your team in repetitive SEO work, but never letting go of quality or compliance.
Costs and measuring ROI for cybersecurity SEO
Committing budget to SEO in cybersecurity is a big move—but it’s much more than a routine marketing line item. You’re building trust, striving to outrank competitors, and capturing those all-important high-value leads. Of course, because the sector is so technical and regulated, getting an accurate sense of costs and returns means clear strategy upfront. Choose the right investment model, and you turn spend into lasting authority and measurable growth.
SEO cost models: self-serve, agencies, and automation
So, where do you start? Cybersecurity firms have several models on the table. Self-serve tools run on monthly subscriptions and are brilliant for experienced in-house teams—giving you control over keyword research and technical checks at low cost.
Agency retainers suit firms seeking end-to-end SEO management, often on a rolling basis. These bring sector expertise and save internal resources but cost more. If you need to fix a particular challenge—maybe a site migration or compliance project—pay-per-service solutions mean you pay for a defined outcome, no long-term commitment.
And then there’s performance-based SEO: fees depend on results like rankings or qualified leads, so you pay more as you win. For risk-averse firms, this offers cost certainty, but demands careful compliance vetting for the sector.
| Model | Cost Range | Best For | Pros | Cons |
|---|---|---|---|---|
| Self-serve tools | £50–£500/mo | Small firms, skilled teams | Control, flexibility | Requires expertise |
| Agency retainer | £1,000–£10,000+/mo | Enterprise, ongoing needs | Expertise, hands-off | Higher cost |
| Pay-per-service | £500–£7,000+/project | Targeted projects | No ongoing fee | No continuity |
| Performance-based | Outcome-driven | Risk-mitigation | Lower upfront cost | Result-dependent |
If compliance and technical demands are always looming, opt for models with real cyber expertise and rapid response.
KPIs to measure SEO ROI in cybersecurity
But how do you track real results? Traffic is just the start; Marketing and Sales Qualified Leads (MQLs/SQLs) show you’re connecting with buyers who matter. Measure organic sessions, time on page, bounce rates, and—crucially—conversion rates and closed deals.
The best signs? Growth in high-quality backlinks, keyword ranking rises, and direct link between SEO and new pipeline business.
Value of continuous analytics and maintenance
Regular analysis keeps spend smart and mitigation strong. Frequent audits, up-to-date content, and compliance reviews guard both technical health and reputation.
In cybersecurity SEO, continuous improvement isn’t optional—it’s your safeguard for trust, lead quality, and true ROI.
How to choose the right SEO tools and services for cybersecurity
Evaluation criteria specific to cybersecurity needs
Selecting SEO solutions for cybersecurity firms is about much more than finding a platform with a flashy dashboard or a long feature list.
You need a partner that truly understands cybersecurity—sector experience, technical prowess, and compliance are absolutely crucial. The truth is, general digital marketing results simply won’t cut it in this space.
Focus on vendors that offer actual cybersecurity case studies and clearly put compliance, like GDPR, front and centre—not as an afterthought.
- Security and compliance expertise
Insist on clear sector case studies and a compliance-first approach throughout. - Automation and technical audits
Prioritise platforms offering automated checks, SSL/schema monitoring, and hassle-free workflows. - Analytics and CRM integration
Smooth integration lets you actually measure ROI and report on what matters.
Overview of leading SEO tools for cybersecurity
So, which platforms actually deliver for cybersecurity companies? There’s a mix of trusted industry giants and sector-specific newcomers vying for attention.
Ahrefs and SEMrush earn their stripes with rigorous audits and top-notch keyword intelligence. But tools like Tely AI specialise in automation tailored to security nuances. And don’t overlook Google Search Console—free, yet invaluable for both site health and security issues.
If you’re sizing up a new agency or platform, look for tangible security industry results—not just generic digital marketing wins.
| Platform/Agency | Security/Compliance | Automation/Tech Features | Analytics/CRM Integration | Sector Expertise | Notable Differentiators |
|---|---|---|---|---|---|
| Ahrefs | Strong | Moderate | Excellent | Widely used | Backlink/keyword data strength |
| SEMrush | Strong | Moderate | Excellent | Compliance focus | Comprehensive audits |
| Tely AI | Sector-specific | High | Good | Cybersecurity focus | AI-powered content/lead ID |
| Google Search Console | High | Low | Good | Universal | Free, security insight |
| Others (e.g. SEOSwarm, SearchAnalytics.ai) | Varies | Varies | Varies | Check references | Request sector case studies |
Let this table focus your search—whether it’s automation, analytics, or proven cybersecurity know-how that matters most.
Key questions to ask when vetting solutions
A few pointed questions will save time and effort down the line.
- Compliance experience
Has the provider served clients with similar compliance demands? - Automated checks
Does the tool automate both SEO and security essentials? - Data integration
Are analytics and CRM tools truly integrated for unified reporting? - Security audits
Do you get regular, automated security audit reports? - Proven sector outcomes
Can the provider show sector-specific case studies or results?
Choose providers that prove their cybersecurity expertise, compliance strength, and automation. Those are the essentials for risk-aware, high-growth SEO in this sector.
Common SEO mistakes and risks for cybersecurity companies to avoid
Ignoring technical SEO and website security
Ever wondered why a small technical lapse causes such massive fallout in cybersecurity SEO? It’s more than just a maintenance chore. Failing to update plugins or patch software exposes your site to breaches—and those glaring browser warnings that instantly scare away visitors.
Trust is everything in this sector. Neglecting HTTPS, slow page speeds, or weak mobile optimisation won’t just frustrate users—it tanks your rankings with Google too. Misconfigured firewalls or CDNs can even block your pages from being indexed at all.
Once trust is lost, regaining it takes time. For cybersecurity brands, that’s a risk you can’t afford.
Overlooking EEAT and content credibility
Here’s the thing: thin, outdated, or incorrect technical advice does real harm. If you don’t show author credentials, up-to-date certifications, and transparent compliance references, your authority vanishes—and your rankings follow.
Publishing unverified or non-compliant guidance creates even bigger problems. You might run into serious compliance risks and see your site penalised in search. Every page must reflect authentic, current expertise—there’s zero margin for error.
Scaling too quickly without quality control
Tempted to churn out content rapidly? That’s a classic misstep. Without robust review, duplicate pages creep in, triggering SEO penalties and confusing potential clients.
When editorial checks go ignored and “more” overtakes “better”, accuracy and alignment with buyer intent disappear. Sustainable results require regular audits and an unwavering commitment to quality.
Recap: Data Table—Summary of Common SEO Risks
| Risk Area | Frequent Error | Impact | Solution |
|---|---|---|---|
| Technical SEO | Unpatched software, weak HTTPS | Lost trust, lower rankings | Regular updates, SSL monitoring |
| EEAT & Content | Thin/outdated content, no credentials | Loss of authority, compliance risks | Expert-led, up-to-date material |
| Scaling | Duplicate or unchecked content | SEO penalties, confused users | Audit, editorial review |

AI-Powered Content Strategy
See the AI platform that's replacing entire content teams (with better results).
My Final Thoughts on Cyber Security SEO
Trust isn’t just a buzzword in cybersecurity SEO—it’s the currency that drives every click, lead, and deal. I’ve seen too many firms lose ground by treating SEO as a checklist, not a discipline. The real winners are those who combine technical rigour, expert-driven content, and visible trust signals at every touchpoint.
If you’re serious about results, here’s what I recommend: • Audit your technical SEO and security—no shortcuts. • Build content with real experts, not just marketers. • Refresh compliance signals and certifications regularly. • Use automation, but never skip human oversight.
SEO for cybersecurity isn’t a one-off project—it’s a living system that should evolve as threats and buyer expectations change. Authority and trust are earned day by day, update by update. In this industry, credibility is your greatest asset—and it’s always on display.
— Wil